What Is OAuth 2.0 and Why Is It Critical for Secure Access?

- Key Points:
- OAuth is a protocol that allows secure access to user data without sharing passwords.
- It seems likely that OAuth 2.0 is the most widely used version due to its flexibility for web, mobile, and IoT apps.
- The Authorization Code Flow is generally considered the most secure for web applications.
- OAuth enhances cybersecurity by supporting the CIA triad (Confidentiality, Integrity, Availability).
- While powerful, OAuth’s security depends on proper implementation to avoid vulnerabilities.
What is OAuth?
OAuth is like a digital bouncer that lets apps access your data without needing your password. It’s an open standard for authorization, widely used to let you log into apps using your Google, Facebook, or GitHub accounts. Instead of sharing your credentials, OAuth uses tokens to grant limited access, keeping things secure and user-friendly.
Why Developers Love It
For developers, OAuth is a lifesaver. It means you don’t have to store user passwords (a security nightmare) and users don’t have to remember yet another login. It’s a win-win: secure access for apps and a smooth experience for users.
How It Works
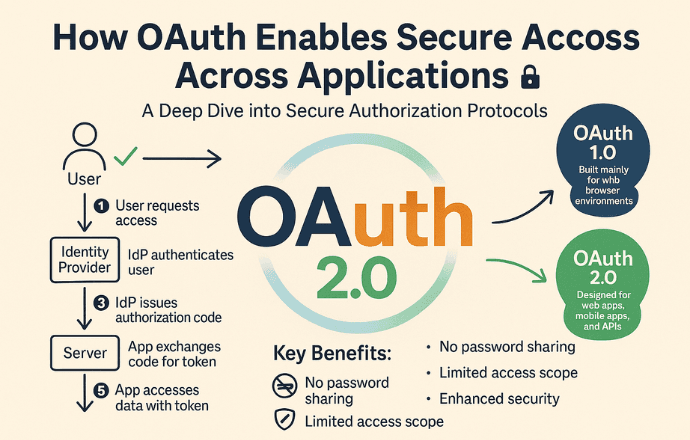
Imagine you’re at a concert. You show your ID to get a wristband (token) that lets you into VIP areas. OAuth works similarly: you log into an Identity Provider (like Google), approve access, and the app gets a token to access your data. No password sharing, no fuss.
Why It Matters
OAuth aligns with cybersecurity principles like the CIA triad—keeping data confidential, untampered, and available. It’s a cornerstone of modern network security, ensuring apps can communicate safely across the internet.
What is OAuth?
OAuth is an open-standard protocol for authorization. It lets a third-party app access a user’s data without ever touching their password. Think of it as a digital middleman that hands out temporary keys (tokens) to unlock specific doors (data) without giving away the master key (your password).
There are two main versions:
- OAuth 1.0: The older, clunkier version, mostly used in the early days of the web.
- OAuth 2.0: The modern, flexible standard that works for web apps, mobile apps, and even IoT devices. It’s the one you’ll likely use today.
OAuth 2.0 is the industry darling because it’s simpler and supports a variety of use cases. It’s like the Swiss Army knife of authorization—versatile, reliable, and widely adopted.
The Three Players in the OAuth Game
OAuth involves three key players, each with a distinct role. Picture a nightclub scenario to make it fun:
- User (Resource Owner): That’s you, the VIP who owns the data (like your Google Calendar or GitHub repos). You decide who gets access to your exclusive party.
- Server (Client/Application): This is the app that wants to crash your party. It’s hungry for your data but needs your permission to get in.
- Identity Provider (IdP): The bouncer at the door (think Google, Facebook, or GitHub). They check your ID, confirm you’re legit, and hand out wristbands (tokens) to the app.
These three work together to ensure secure, seamless access without anyone sharing sensitive info.
OAuth 1.0 vs. OAuth 2.0
Let’s quickly compare the two versions:
| Feature | OAuth 1.0 | OAuth 2.0 |
|---|---|---|
| Complexity | More complex, with cryptographic signatures | Simpler, uses HTTPS and tokens |
| Use Cases | Mainly web browsers | Web, mobile, IoT, APIs |
| Security | Secure but cumbersome | Secure with proper implementation |
| Adoption | Largely deprecated | Industry standard |
OAuth 2.0 is the go-to because it’s easier to implement and supports modern apps. OAuth 1.0? It’s like using a flip phone in the smartphone era—functional but outdated.
How the OAuth Flow Works
Let’s zoom in on the Authorization Code Flow, the most secure and popular flow for web apps. Here’s how it goes down, step by step, with a real-world example (say, logging into a photo-editing app with your Google account):
- You want access: You click “Log in with Google” on the photo app’s website.
- App redirects to IdP: The app sends you to Google’s login page.
- You authenticate: You enter your Google username and password (the app never sees this).
- You grant permission: Google asks, “Hey, can this app access your photos?” You click “Allow.”
- IdP sends an authorization code: Google redirects you back to the app with a temporary code.
- App exchanges code for a token: The app sends this code (plus its own secret credentials) to Google to get an access token.
- App uses the token: The app uses the token to fetch your photos from Google’s servers.
It’s like getting a backstage pass at a concert. You show your ID once, get a pass, and use it to access the VIP area—without handing over your driver’s license.
Types of OAuth 2.0 Flows
OAuth 2.0 offers four main flows, each tailored to specific scenarios:
- Authorization Code Flow: The gold standard for web apps. It’s secure because it uses a client secret (a private key only the app knows). Best for server-side apps where secrets can be safely stored.
- Implicit Flow: Used for browser-based apps (like single-page apps) where secrets can’t be hidden. It’s less secure, so use it sparingly.
- Client Credentials Flow: For machine-to-machine communication, like an app accessing its own data (no user involved). Think of two servers chatting securely.
- Resource Owner Password Credentials Flow: The user hands over their username and password directly to the app. This is discouraged because it’s less secure—avoid it unless absolutely necessary.
For most developers, the Authorization Code Flow is the way to go. It’s like choosing a sturdy lock for your front door—reliable and secure.
Why OAuth is a Developer’s Secret Weapon
OAuth is a game-changer for developers. Here’s why it’s your new best friend:
- No Password Storage: You don’t have to store user passwords, reducing the risk of a data breach. It’s like not keeping a spare key under the doormat.
- User-Friendly: Users can log in with existing accounts (Google, Facebook, etc.), sparing them the hassle of creating new credentials.
- Scalable Security: OAuth works across platforms—web, mobile, IoT—making it versatile for any project.
- Standardized: With libraries and tools for every major programming language, you can implement OAuth without reinventing the wheel.
Plus, OAuth aligns with the CIA triad, a cornerstone of cybersecurity:
- Confidentiality: Only authorized apps access user data.
- Integrity: Tokens are cryptographically signed to prevent tampering.
- Availability: OAuth ensures services are accessible without compromising security.
This makes OAuth a key player in network security, protecting data as it zips across the internet.
Best Practices for Implementing OAuth
Ready to add OAuth to your app? Here are some pro tips to keep things secure and smooth:
- Use HTTPS Everywhere: Encrypt all communications to protect tokens from eavesdroppers. It’s like sending your secrets in a locked vault.
- Validate Tokens: Always check that tokens are legit and haven’t been tampered with.
- Short-Lived Tokens: Make access tokens expire quickly (e.g., in an hour) to limit damage if they’re stolen.
- Use Refresh Tokens: These let you get new access tokens without bugging the user for permission again.
- Secure Client Secrets: Keep client secrets (for confidential apps) locked away, like a treasure in a safe.
- Implement PKCE for Public Clients: For mobile or browser apps, use Proof Key for Code Exchange (PKCE) to prevent code interception.
Follow these, and you’ll be building secure apps like a cybersecurity rockstar.
Related: Cybersecurity Secrets REVEALED With CIA, PDR, and PPT Acronyms?
Top Tools and Libraries for OAuth
No need to code OAuth from scratch—there are tons of libraries to make your life easier. Here are some favorites:
| Language | Library | Why It’s Great |
|---|---|---|
| Python | Authlib | Flexible, supports OAuth 2.0 and OpenID Connect. |
| JavaScript | Passport.js | Easy to integrate with Node.js apps. |
| Java | Spring Security OAuth | Robust for enterprise-grade apps. |
| .NET | IdentityServer4 | Comprehensive for ASP.NET projects. |
These tools handle the nitty-gritty of OAuth, so you can focus on building awesome features.
Real-World Example: Authorization Code Flow in Action
Let’s say you’re building a web app that lets users import their GitHub repos. Here’s how the Authorization Code Flow would work:
- User clicks “Connect with GitHub” on your app.
- Your app redirects them to GitHub’s authorization page (
https://github.com/login/oauth/authorize). - User logs in and approves access.
- GitHub redirects back to your app with a code (e.g.,
https://yourapp.com/callback?code=abc123). - Your app sends the code and client secret to GitHub’s token endpoint (
https://github.com/login/oauth/access_token). - GitHub responds with an access token.
- Your app uses the token to fetch the user’s repos via GitHub’s API.
It’s a smooth, secure process that keeps everyone happy.
OAuth and Network Security
OAuth isn’t just about convenience—it’s a powerhouse for network security. By using tokens instead of passwords, it reduces the attack surface. It also supports the CIA triad, ensuring:
- Confidentiality: Only authorized apps get access.
- Integrity: Tokens are signed to prevent tampering.
- Availability: Services stay accessible without compromising security.
While the user mentioned “PDR” and “PPT” acronyms, these aren’t standard in cybersecurity (I checked!). They might be specific to a niche context, but the CIA triad is the real star here, and OAuth nails it.
Conclusion
OAuth is your ticket to building secure, user-friendly apps that play nicely with other services. Whether you’re pulling data from Google, connecting to GitHub, or building the next big thing, OAuth lets you do it without compromising security or user experience. It’s like having a trusty sidekick that handles the hard stuff while you focus on coding awesome features.
So, grab one of those libraries, follow the best practices, and give OAuth a spin in your next project. Your users will thank you for sparing them another password to remember, and your app will be a fortress of security. Now, go forth and code with confidence!
Related: What Is a Proxy Server? A Beginner’s Guide to Internet Privacy
FAQ
- What’s the difference between OAuth and OpenID Connect?
OpenID Connect builds on OAuth 2.0 to add authentication. OAuth handles authorization (access to data), while OpenID Connect verifies who the user is. - Can I use OAuth for mobile apps?
Absolutely! The Authorization Code Flow with PKCE is perfect for mobile apps, adding extra security for public clients. - Is OAuth secure?
When implemented correctly, OAuth is very secure. But poor implementation (like not using HTTPS) can leave vulnerabilities, so follow best practices. - Do I need to pay to use OAuth?
Nope! OAuth is an open standard, and most IdPs like Google or GitHub offer free tiers for developers. - Can I set up my own Identity Provider?
Yes, but it’s complex. Using established IdPs like Google, Facebook, or Auth0 is usually easier and more trusted. - Why is the Authorization Code Flow so popular?
It’s the most secure flow for web apps, using a client secret and temporary codes to prevent unauthorized access. - How does OAuth help with cybersecurity?
OAuth supports the CIA triad by ensuring data confidentiality, integrity, and availability, making it a key tool for secure app communication.
Sources We Trust:
A few solid reads we leaned on while writing this piece.